What is Vulnerability Management? How to Avoid Vulnerability in a Magento Store
- March 24, 2025
- Posted by: Tony
- Categories: Blog, Magento

As our dependence on technology increases so do the number and type of devices, applications, tools, and hardware. Combining hardware with software applications makes for a complex mix that may be on the cloud, on-premise, or hybrid.
Managing a growing and complex amalgamation of devices and applications is a huge task and has more than a few digital vulnerabilities. The sheer scale of management makes security an exclusive task that organizations need to plan, execute, and continuously monitor.
As the e-commerce industry expands, hackers find it increasingly lucrative to attack websites, steal data, or demand ransoms.
Incidents are becoming increasingly common, can cost thousands of dollars to resolve, and many cause organizations to go under. If cybersecurity vulnerability management is not on the list of tasks in your e-commerce organization, you need to add them now.
This is especially true for Magento e-commerce stores as it is the most widely used e-commerce platform in the industry.
What is Vulnerability Management?
Vulnerability management refers to the processes, tools, and strategies to identify, evaluate, treat, and report security vulnerabilities and misconfigurations within software and systems.
In an e-commerce context, the vulnerability management process allows the business to monitor their digital environment to identify risks and get an up-to-the-minute view of its security status.
Vulnerabilities can exist across endpoints, workloads, and systems, and hackers exploit these to access restricted systems and applications to cause damage and hinder the business.
Identifying vulnerabilities in various systems, networks, and application requires tools such as a vulnerability scanner, a program designed to review digital systems and uncover potential weaknesses, making vulnerability management possible.
Risk-based vulnerability management programs address weaknesses in software, hardware, and other infrastructure. It uses machine learning to extend vulnerability management beyond traditional IT assets, incorporating cloud infrastructure, IoT devices, web apps, and more.
This enables the business to access insights across its entire attack surface. Risk-based vulnerability management facilitates accurate, risk-based prioritization so that the business can identify and repair the weaknesses that are most likely to result in a breach.
Managing vulnerabilities is an always-on, proactive, and ideally automated process that seeks to keep digital infrastructure such as computers, networks, and enterprise applications safe from cyberattacks and data breaches. It is a crucial part of a comprehensive security program.
Cybersecurity vulnerability management seeks to reduce the organization’s risk exposure by mitigating as many vulnerabilities as possible. This is not an easy task, given the number of applications, devices, tools, and programs used. Vulnerability management needs to be an organized and continuous effort as new threats constantly emerge.
The Various Aspects of Vulnerability Management
All vulnerabilities are not the same in seriousness and the Common Vulnerability Scoring System (CVSS) is a free and open industry standard that cybersecurity organizations use to assess and communicate the severity and characteristics of software vulnerabilities.
The CVSS Base Score ranges from 0.0 to 10.0 and is as follows:
| CVSS Score | Severity Rating |
| 0.0 | None |
| 0.1-3.9 | Low |
| 4.0-6.9 | Medium |
| 7.0-8.9 | High |
| 9.0-10.0 | Critical |
Vulnerability management offers several tools and solutions to deal with threats and enhance safety. A robust management program usually has the following components:
- Asset discovery and inventory — management of thousands of devices, software, and servers can be impossible without an asset inventory management system. IT departments use this system to track and maintain IT infrastructure across locations and usage.
- Vulnerability scanners — test systems and networks for vulnerabilities and try to access passwords and user accounts.
- Patch management software — enables e-commerce organizations to keep their computing infrastructure updated and equipped with the latest security patches. Most solutions automatically check for updates with a predetermined frequency.
- Security configuration management (SCM) tools — ensure changes to device security settings are tracked, approved, and compliant with security policies. SCM tools also allow organizations to scan their devices and networks for vulnerabilities, remediate, and report on security compliance.
- Security incident and event management (SIEM) software — consolidates security information and events in real-time and gives IT complete visibility into the organization’s security infrastructure, including network traffic, device activity, and user activity.
- Penetration testing software — enables IT to identify vulnerabilities, simulate attacks and test the organization’s ability to withstand an attack.
- Threat protection software — ensures organizations can track, monitor, analyze, and prioritize potential threats for better protection.
- Remediation — prioritizes vulnerabilities, identifies appropriate next steps, and generates remediation tickets for IT teams to better manage a response.
You can also read this blog post, “Magento Security Scanner to Find Vulnerabilities & Malware” >>
Difference between Vulnerability Management and Vulnerability Assessment
Vulnerability management is the process of monitoring for dangers to the website, applications, tools, and other digital property of the business. A vulnerability assessment management is a one-time evaluation of several solutions or the entire network, though it can be periodic.
The assessment can be done by an external consultant who will hand over a report after the vulnerability assessment. Vulnerabilities will be listed based on their technical severity and include suggested remedial action.
There are several types of vulnerability scans, some are listed below:
- Network scan to check the strength of the network to withstand a cyber attack.
- Host scan that locates vulnerabilities in computers, servers, and networks.
- Wireless network scan to monitor the organizations’ wi-fi network.
- Web application scan to identify vulnerabilities and web applications that may not have been configured correctly.
In a dynamic security environment, organizations should do a vulnerability assessment at fixed periods to ensure their IT infrastructure is continually updated and secure.
6 Steps in Vulnerability Management
To be effective, vulnerability assessment management needs to be a comprehensive set of steps that can be repeated:
Discovery
Prepare an asset inventory of all devices, hardware, software, and shadow devices that can be vulnerable.
Ensure you have company-wide buy-in for this inventory process.Only a comprehensive asset inventory will ensure you identify even the slightest opportunity for a threat.
Also, do a root cause analysis to better understand the vulnerability. This enables better prioritization and remediation.
Prioritize
Each application within the organization must be reviewed for criticality towards ongoing business operations, and how it can impact business continuity, reputation, and financial position of the company if attacked.
Usually, vulnerability is prioritized into high, medium, and low impact. These assets contain sensitive data and based on the level of impact will need multiple layers of protection to prevent a breach.
While prioritizing risk also identify objectives, KPIs, and quantifiable metrics to report progress and measure the success of the vulnerability management program.
Assess vulnerability
The discovery and prioritization process may help your organization identify potential vulnerabilities. Compile a list of recommendations to deal with these vulnerabilities and have clear instructions for the remediation action to decrease the risk.
Remediate and verify remediation
Create a plan that lists various remediation actions and their responsible owners. A progress tracker maps key milestones and progress to confirm that corrective action is underway.
A prioritized vulnerability list helps an e-commerce company decide to accept the risk of the vulnerable asset, engage in immediate or delayed remediation, mitigate the vulnerability, or remove it.
Organizations can accept the risk for non-critical assets but delaying remediation for critical assets may not be a wise decision. A mitigation plan recognizes vulnerability and makes it harder for hackers to exploit it.
An organization’s goal is always to do away with high-risk vulnerabilities that could affect business-critical assets. Verify that the remediation actions actually work, reduce the size of the surface that can be attacked, and increase transparency and accountability in the security program.
Report
Put in place a clear matrix on the reporting processing and chain of communication when a vulnerability is detected, a breach is recorded, or an attack is noticed.
Create a detailed contact list depending on the intensity of the problem so that the right people are notified and corrective action is taken in a timely manner.
Put in place a continuous reporting mechanism so that the required management is aware of the security status and willing to make the investment to continue security enhancement.
Continuous improvement
Vulnerability management is cyclic in nature. It involves testing, feedback, and continuous improvement of critical and non-critical assets. The security effort has to be around researching and strengthening weak areas and proactively preventing vulnerabilities.
An organization needs to constantly improve its security controls, policies, and procedures as new threats emerge.
Once an organization has put in place a cybersecurity vulnerability management assessment program, below are some ways to go about improving it.
How to Improve the Vulnerability Management Process
Here are some best practices to shore up the vulnerability of an organization.
- Scan all devices and applications regularly — Put in place a cadence that requires all devices in the organization to be scanned at a predefined frequency. This periodic scanning will reveal vulnerabilities that can then be proactively addressed.
- Assign asset owners — to a hardware or software asset to increase accountability in the vulnerability management process. List the activities each owner is responsible for, such as patching, maintaining updated versions, monitoring for safety, reporting, etc.
- Maintain strong documentation — when assets are scanned, track their vulnerability and remedial action. Documentation helps an organization verify that its security is up-to-date and closely monitored.
- Train teams in security practices — so that they can accurately assess and implement solutions if they detect vulnerabilities.
- Define, measure, and review security program metrics — use baseline information on applications to measure and understand risk, create awareness among the security team on required facets of security, and organize training where necessary.
- Automate scanning and asset management processes — so that these processes swing into action without human intervention.
Vulnerability Issues in Magento and How to Avoid Them
When it comes to e-commerce cybersecurity, it is always better to be safe than sorry. The cost of recovering from an incident is just too high and most companies fail to make it through.
There are several vulnerabilities in Magento that the IT department needs to keep an eye on, the most prominent being a ransomware attack.
- XSS or cross-site scripting attack — is the most common Magento security threat. In an XSS attack, hackers exploit a vulnerability and inject malicious codes into the website. An XSS attack enables hackers to steal cookies, hijack sessions, and steal the personal information of customers. Vulnerabilities may arise when passwords are not strong enough or the security patch has not been updated.
- Server attack through code execution— attackers create executable files with common extensions like .csv which are then executed on a Magento server or other applications. Magento releases patches periodically to fix these vulnerabilities. Ensure your website always has the latest patch, strengthen your passwords, and add blockers to fend off a code execution attack.
- SQL injection — attackers insert a harmful SQL code on the website and access or alter the database. Hackers can also change the user permission preventing the admin from accessing administrative files and folders. To enhance website security, owners need to monitor user access and suspicious users with strange names, use automation for monitoring and adopt a firewall.
- CSRF attack — occurs when hackers trick users into executing harmful codes that make the website vulnerable. Attackers usually do this through cookies and ‘post and get’ statements. To prevent CSRF threats, the website admin can install a synchronizer token pattern to verify requests based on the secret key and enable the cookie-to-header token feature, which l flags request from malicious sites.
- Brute force attack — is when hackers use automated programs that engage in trial and error to guess the login credentials of an account. Replace default passwords and user names, and use alphanumeric or phrases as passwords to secure the site. The more complex and lengthy the password, the longer it will take for it to be cracked in a brute-force attack. Change all passwords periodically, use CAPTCHA, and 2-factor authentication for logins, and set security setting to block users if attempts to log in come too frequently from a single IP.
- Credit card hijack — lets hackers install malware and secretly record all the credit cards used on the website. Since they have access to the website, hackers can change the payment address and lead payments to the attacker’s servers. This type of attack can remain undetected for a while leading to a loss of revenue and brand image.
- Website defacement — wherein hackers gain control of the website and leave a message on the homepage. They could also delete files or vandalize other pages on the website.
- Botnetting — wherein hackers take control of the e-commerce website and send out large numbers of emails on behalf of the company. This seriously impacts the brand image.
Here’s how you can protect your website from becoming a victim of an attack
- Periodically check the security configurations and coding.
- Proactively monitor security with penetrative testing and regular vulnerability scans.
- Maintain control over the deployment of security patch applications.
- Sign up for security alerts and install all Magento security patches
- Adopt Magento security extensions.
- Use free scans from the Magento Security Center to monitor security risks
- Deploy a web application firewall
- Enable two-step authentication
The above is just a broad list of vulnerabilities and solutions out there. While you focus on your core business, you need a robust technology partner who can ensure the main channels of your revenue are safe and working hard to get you customers.
Reach out to Navabrind IT Solutions to manage the security of your Magento store
Navabrind IT Solutions is a full-stack e-commerce technology provider with over a decade of experience in the industry. We manage website security for several clients, and our global clientele is based all the way from North America, and Europe, to Asia. Our 100+ software engineers have strong technical skills, think strategically, and work thoughtfully instead of just following specifications.
Several of our clients say they partner with us for our ability to work independently. Many have gotten used to our responsive, proactive, high-quality work, quick turnaround time, and on-time deliveries. This has led them to make us their partner of choice for any e-commerce implementation, customization, and maintenance assignments. Our customers say that our work most often exceeds their expectations.
You can partner with us for project-based services, sign up for a retainer, or engage with us on technology-specific assignments. Some clients also partner with us on duration-specific projects such as quarterly, half-yearly, or yearly. Irrespective of what you sign up for, we are deeply committed to maximizing your investment and ensuring your website is always secure.
Reach us to learn more about our expertise in cybersecurity vulnerability management or to begin a conversation about your needs.
Related Articles
-
Post
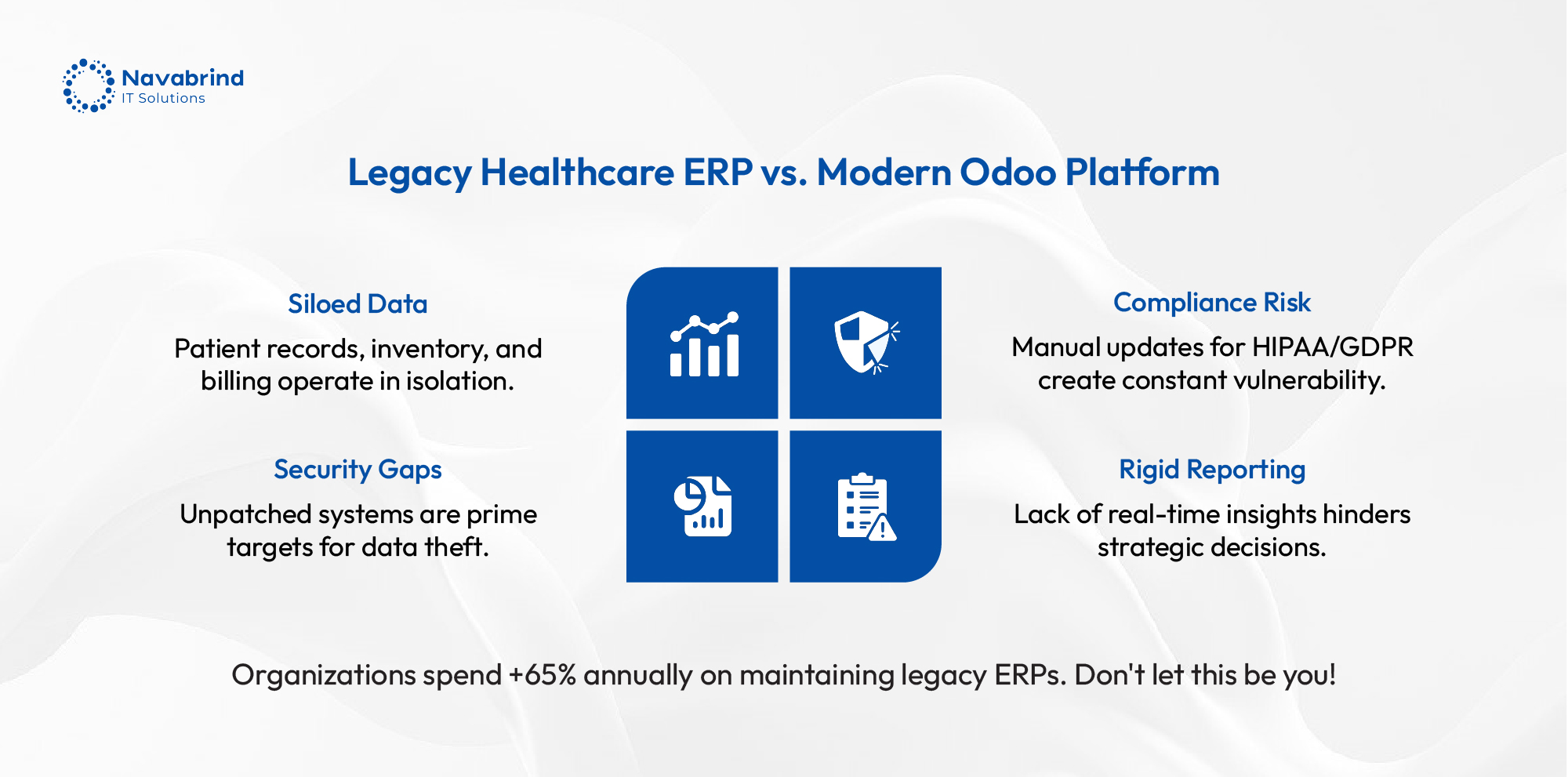
From Legacy Healthcare ERP to Odoo ERP: Why You Need Expert Odoo Migration Help
From Legacy Healthcare ERP to Odoo ERP: Why You Need Expert Odoo Migration Help February 11, 2026 Posted by: Tony Category: Uncategorized No Comments Why Healthcare Organizations Need Odoo ERP Migration Legacy healthcare ERP systems create barriers to efficiency. They are expensive to maintain, and struggle to integrate tools. This disconnect impacts patient care coordination, -
Post
From LLMs to Agentic AI: A Practical Guide to What They Mean and How to Choose
From LLMs to Agentic AI: A Practical Guide to What They Mean and How to Choose February 4, 2026 Posted by: Tony Categories: Artificial Intelligence, Blog No Comments As definitions, use cases, expectations, and investments around Large Language Models (LLMs), Retrieval-Augmented Generation (RAG), AI agents, and agentic AI continue to expand, many individuals and organizations -
Post
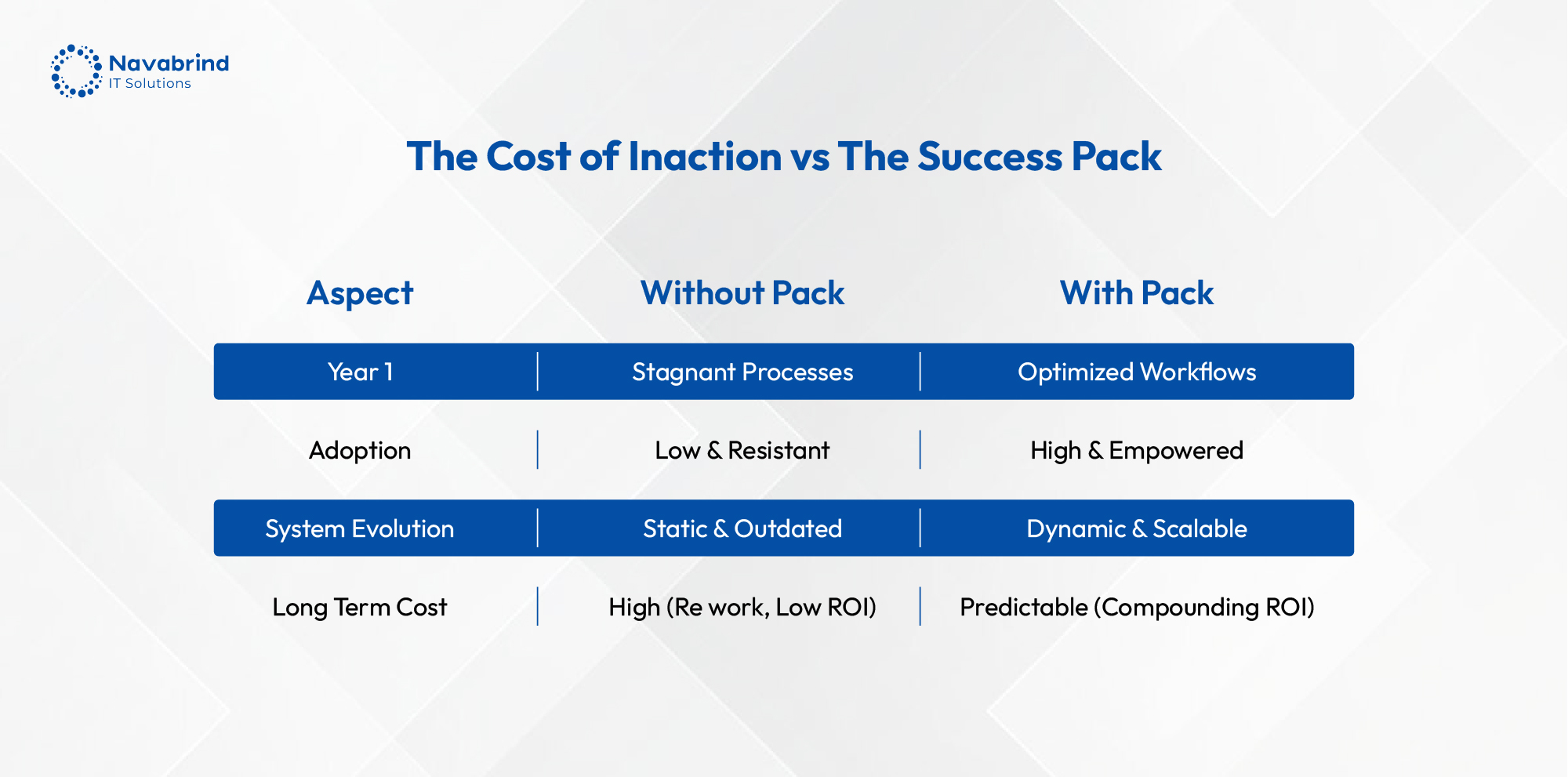
Beyond Go-Live: How Your Odoo Success Pack Drives Real, Long-Term ROI
Beyond Go-Live: How Your Odoo Success Pack Drives Real, Long-Term ROI February 3, 2026 Posted by: Category: Uncategorized No Comments The Implementation Myth Businesses mistakenly measure ERP success by completing the implementation phase while the actual measure of value is the operational transformation unlocked after go-live. The Odoo Success Pack is the framework engineered to
How can we help you?
Get in touch with a solutions consultant that can share best practices and help solve specific challenges.